We will explore how a crypto wallet works in general and find out if our money is truly safe. Did you hear about mnemonic, derivation paths, private and public keys?
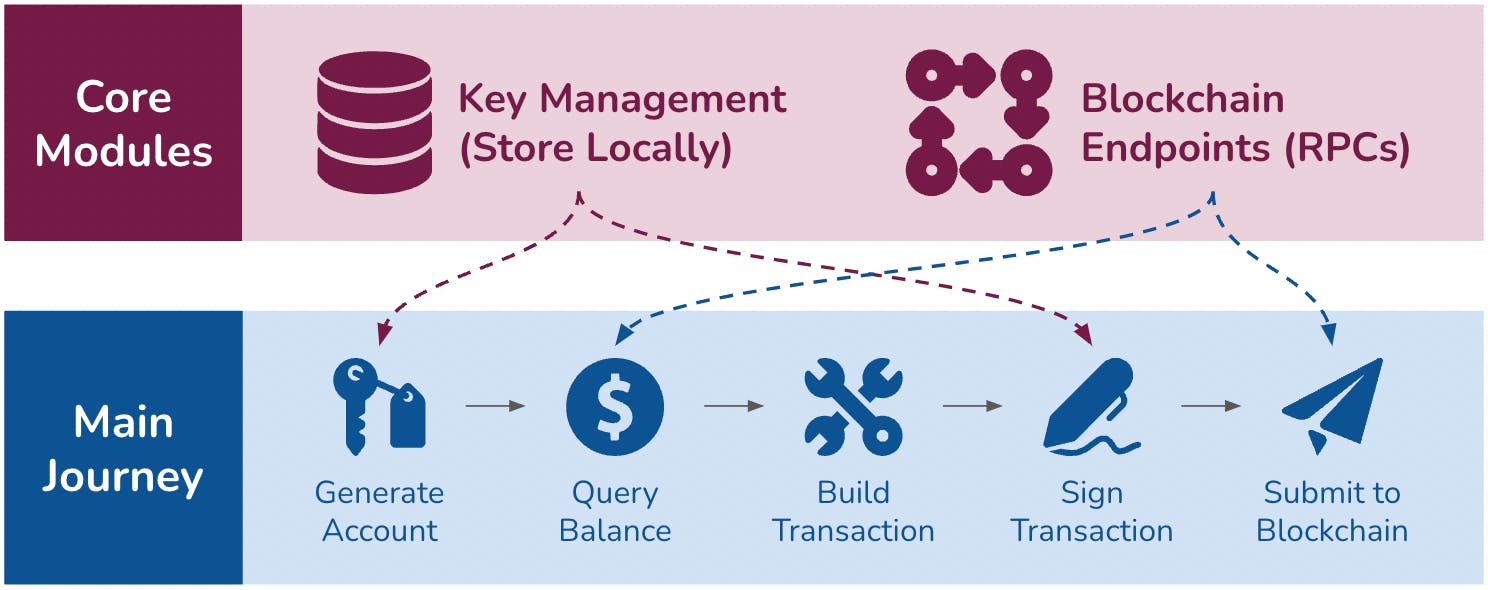
Crypto wallet components
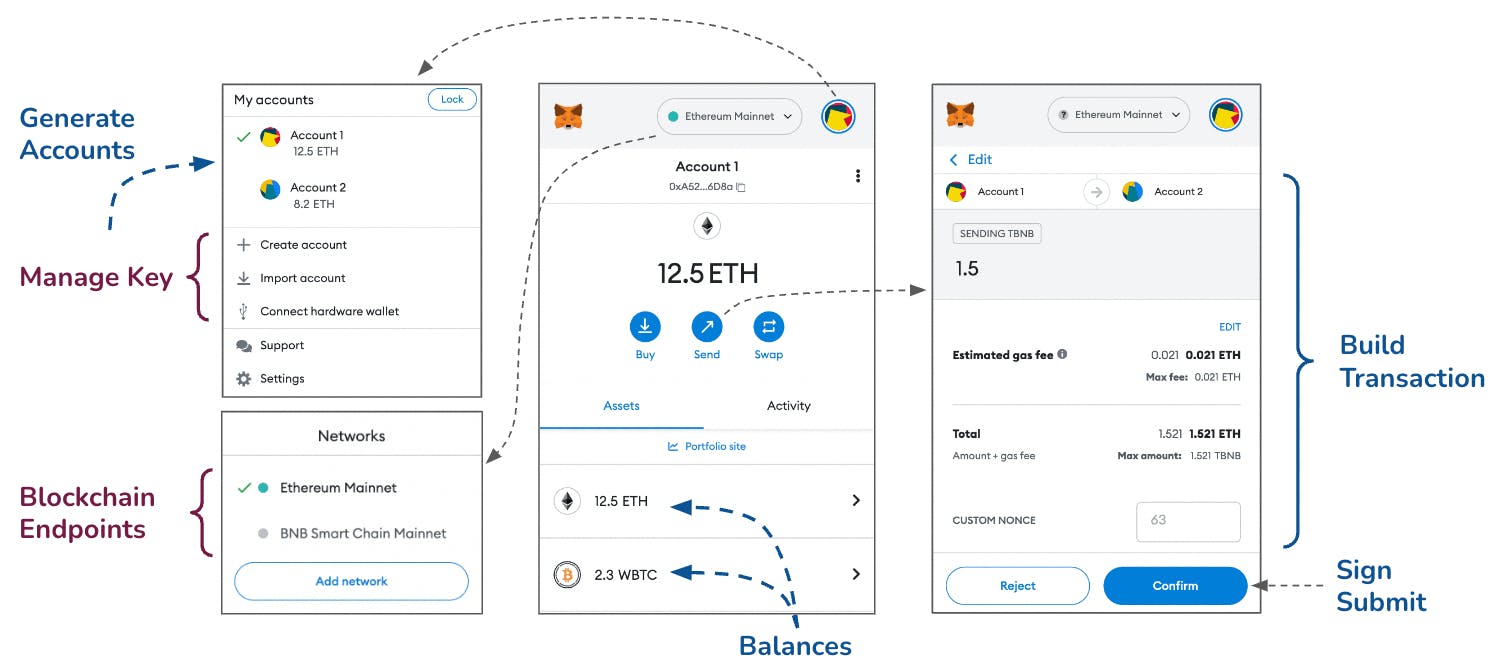
Metamask example:
Key managements
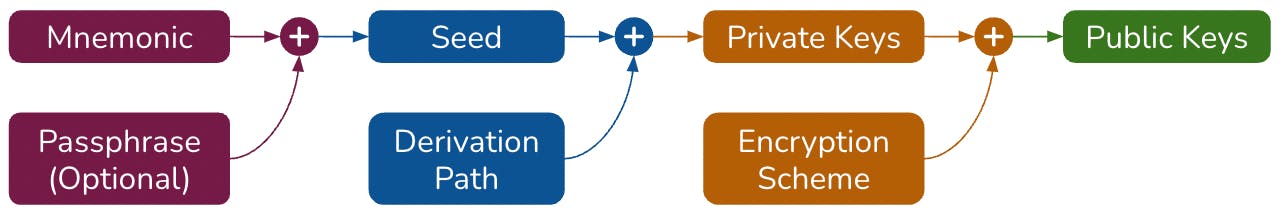
- Mnemonic (BIP39): a group of words, easy to remember, usually 12 or more that are generated when a new crypto wallet is created. It can be used to restore accounts.
- Passphrase (BIP39): an optional feature that can be used in addition to your mnemonic to restrict access to your crypto wallet. It offer extra security in the event that your mnemonic is exposed. It's like two-factor authentication.
- Seed: series of bytes that generated after combining the mnemonic and passphrase.
- Derivation path (BIP32): A derivation path is a piece of data which tells a Hierarchical Deterministic (HD) wallet how to derive a specific key within a tree of keys. Example:
m/44'/60'/0'/0'/0for private key 1 andm/44'/60'/0'/0'/1for for private key 2. - Private keys: a secret number similar to a password. They are used to sign transactions and prove ownership of a blockchain address.
- Encryption scheme: is used to define the algorithm when encrypting transactions or messages.
- Public keys: aka addresses. Each blockchain has a different format.
Derivation path is usually managed by wallets, and encryption scheme is specified by blockchains. As a normal user, we should pay attention to passphrase, mnemonic and private keys.
Passphrase
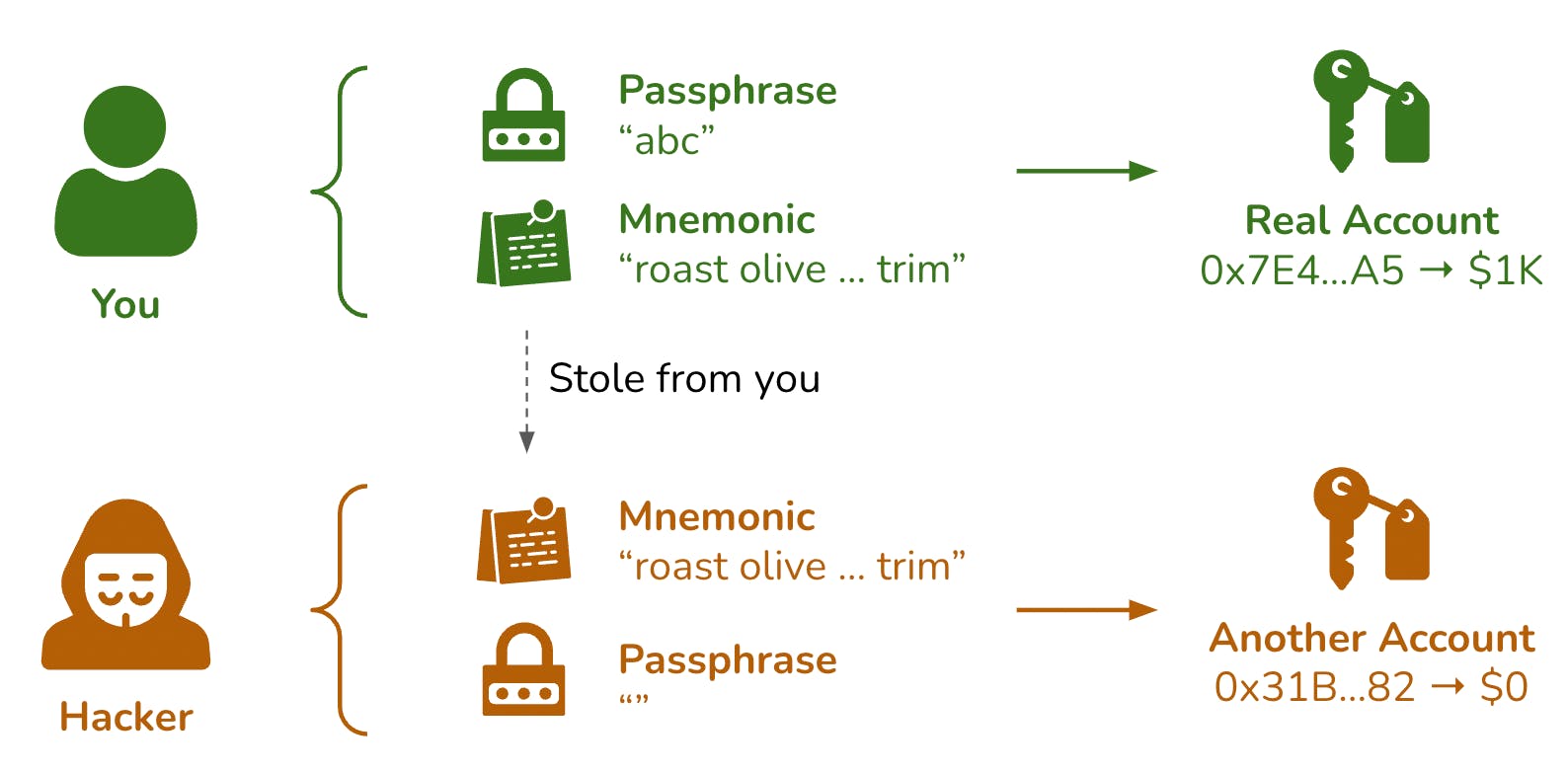
Your passphrase should be short enough to remember it in your mind only. If hackers have mnemonic, they cannot generate the real accounts without the right passphrase.
Mnemonic and Private Keys
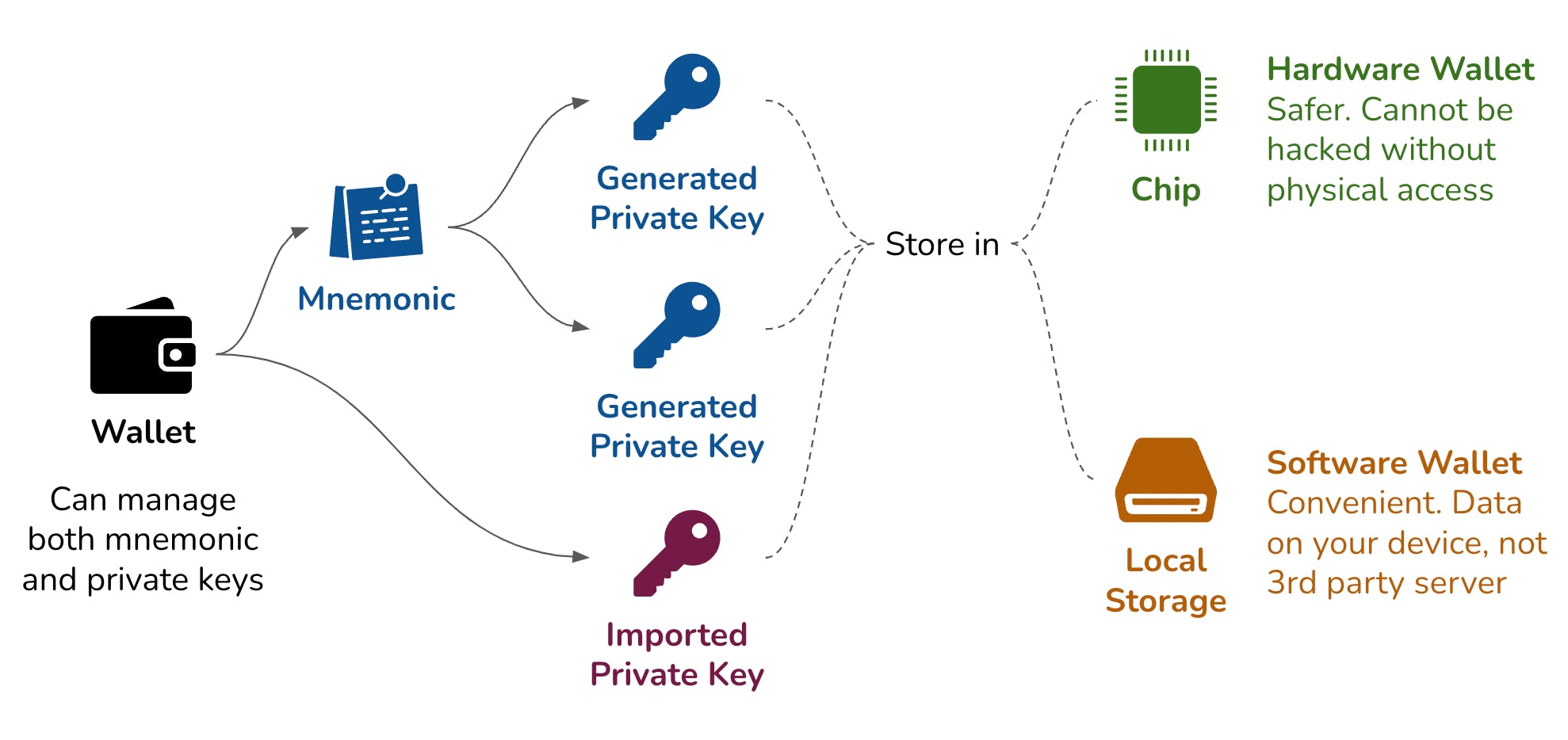
A wallet can import both mnemonic and private keys. After importing:
- Software wallet will store them in your device memory, not in any third party servers.
- Hardware wallet will store in chip. It is safer and cannot be hacked without physical access to the device.
That's all. I hope this post gives you an overview. Thank you for reading my blog.

